The state of Wi-Fi security in 2009
Wireless networks, as we all know, are everywhere today. All the way back in 2004 Denis did a wardriving exercise to check how widespread the use of encryption and other security measures were in wireless networks deployed in and around Leeds.
The arrival of the new JDSU ValidatorPRO-NT NT1155, which includes a wireless detection module (including 802.11n networks), gave me the opportunity to repeat the exercise and see how the situation has changed over the intervening period.
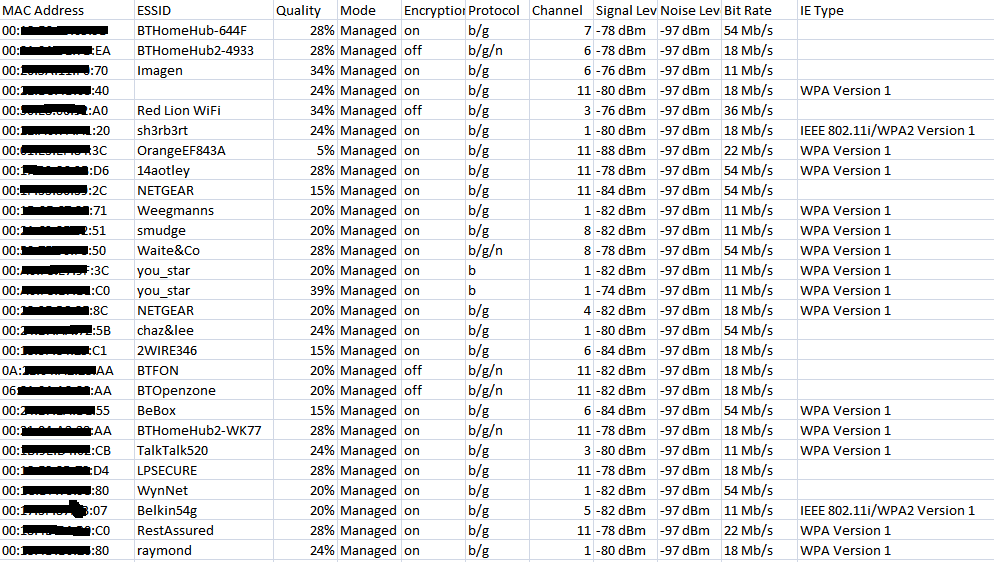
Well, nobody will be surprised to discover that there are even more wireless networks around today. Within 300 metres of our office in a quiet market town ten miles outside Leeds I detected 27 separate networks. Most shops and offices have them and many apartments and homes, thankfully though no banks.
The good news from a security perspective is that most now have some kind of security enabled. This is a big step forward, though I would wager it is in large measure due to manufacturers’ configuring security on by default rather than expecting their users to configure their access points themselves.
All but one network was broadcasting its SSID the vast majority were using the manufacturer default SSID. Strangely most shops and businesses that changed the default seem to view the SSID as an advertising opportunity, making the SSID the business name. I’m not entirely sure this is a good thing, though it must be said that hiding the SSID is hardly the greatest security measure you could take and makes configuring wireless enabled devices that much harder for very little real gain so far as security is concerned.
It would appear that most access points are set to the default channel, 9 of those detected were using channel 11, 7 used channel 1, and 4 were on channel 6. I expect with all this interference on the same channels that the effective throughput may not be as good as it could be.
WPA was the most commonly used encryption, which is also good news and fine for most users. Only one network used WPA2, presumably a new access point/router. Reasonably enough most users will accept whatever security comes preconfigured in their access point.
So judging by this quick test, the situation today is much better than the snapshot taken in 2004. Security is being taken more seriously, at least by the manufacturers. Most new access points come with WPA enabled. It probably always was too much to expect users to configure security for themselves. However there are still plenty of unsecured networks around so using someone else’s bandwidth is still a possibility for those that way inclined.
An easy way to increase your available bandwidth would be to check for other networks close by and ensure that you are not using the same channel. Clearly though very few of the user of wireless around here take the time to configure their wireless at all.
As for the NT1155 Validator it could hardly be easier to use for wireless detection, just select the menu option, let it scan and watch the networks appear. Press the Save button to record the results onto an external USB memory stick in CSV format. It’s a very useful addition to the Validator for those installing and maintaining networks.